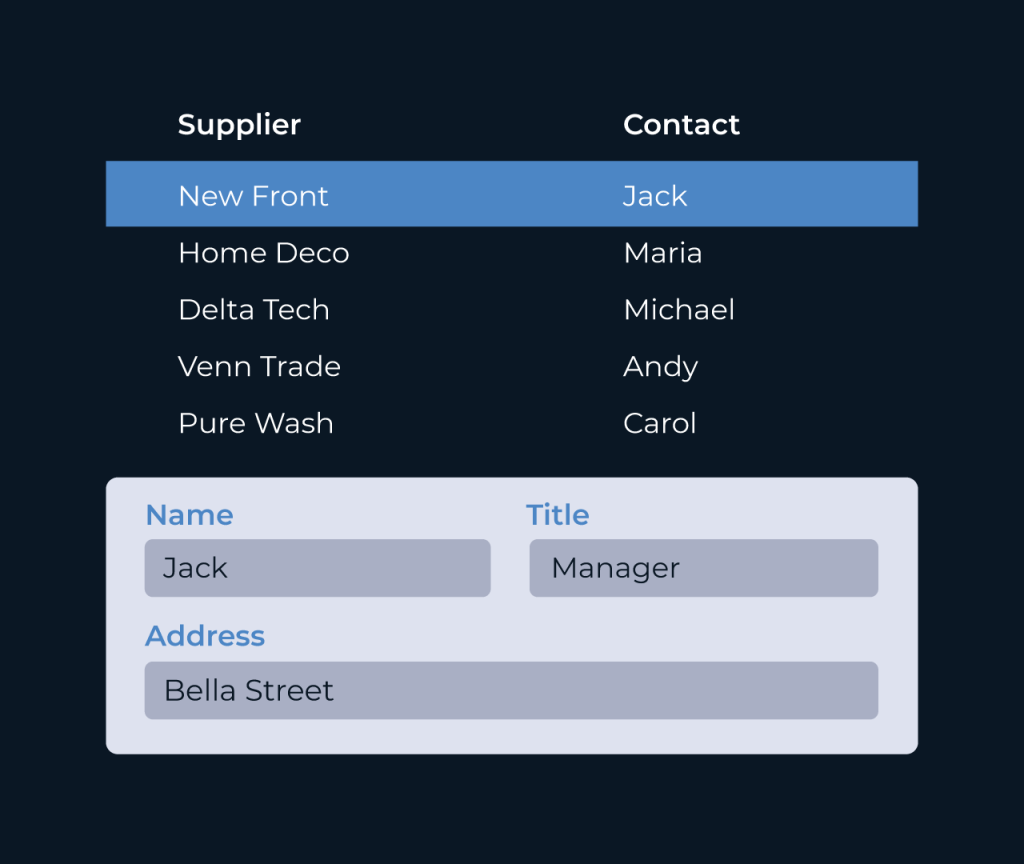
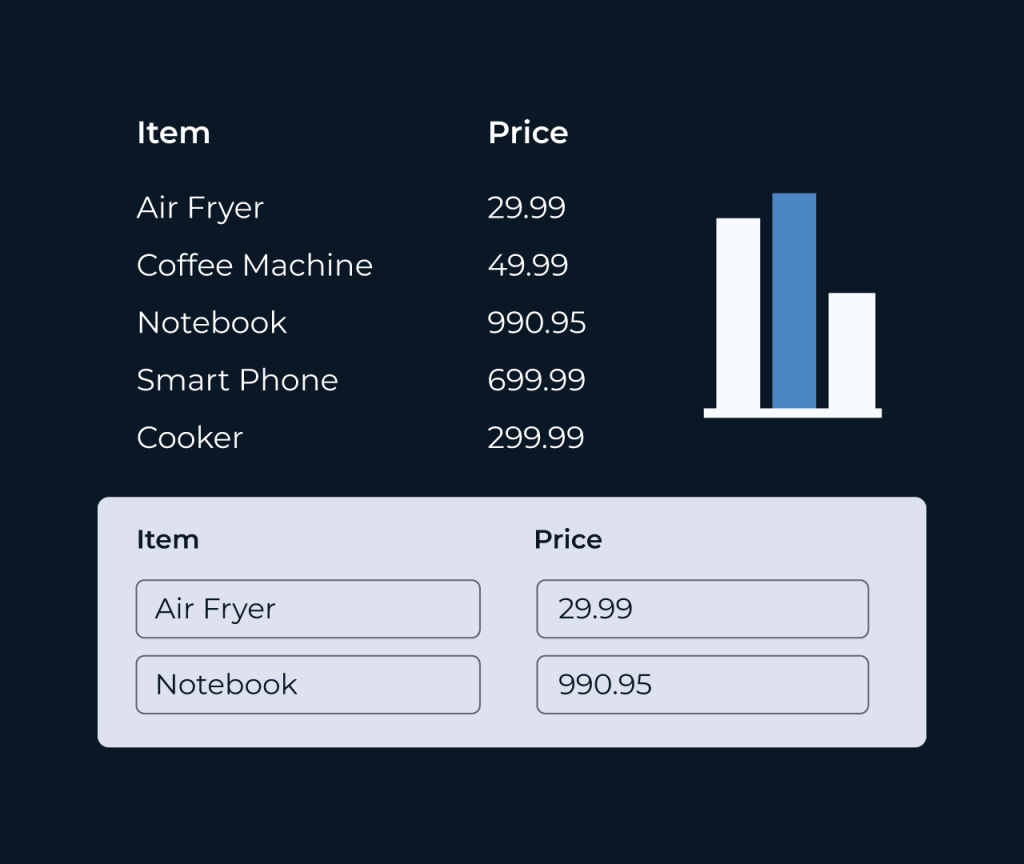
Create a Role Database
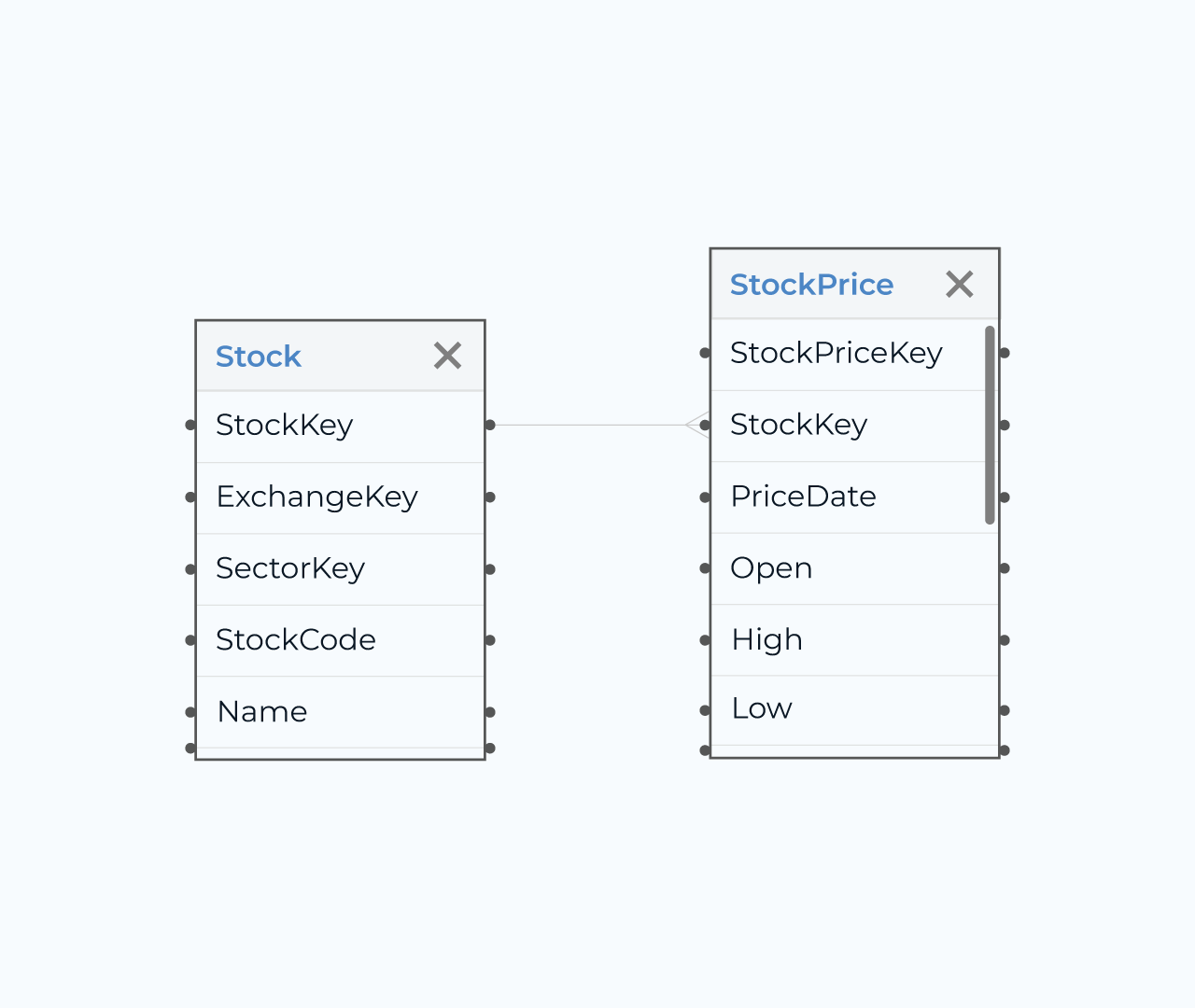
Creating a role database is essential for managing user permissions and ensuring a secure environment. A well-structured role database allows administrators to define roles with specific access rights, streamlining user management and enhancing organization-wide security protocols.
Five simplifies the process of building a role database by offering an intuitive interface and customizable templates. Users can easily define roles, assign permissions, and monitor access levels across their systems. With features like automated updates and role tracking, Five helps organizations maintain compliance and adapt to changing security needs efficiently.