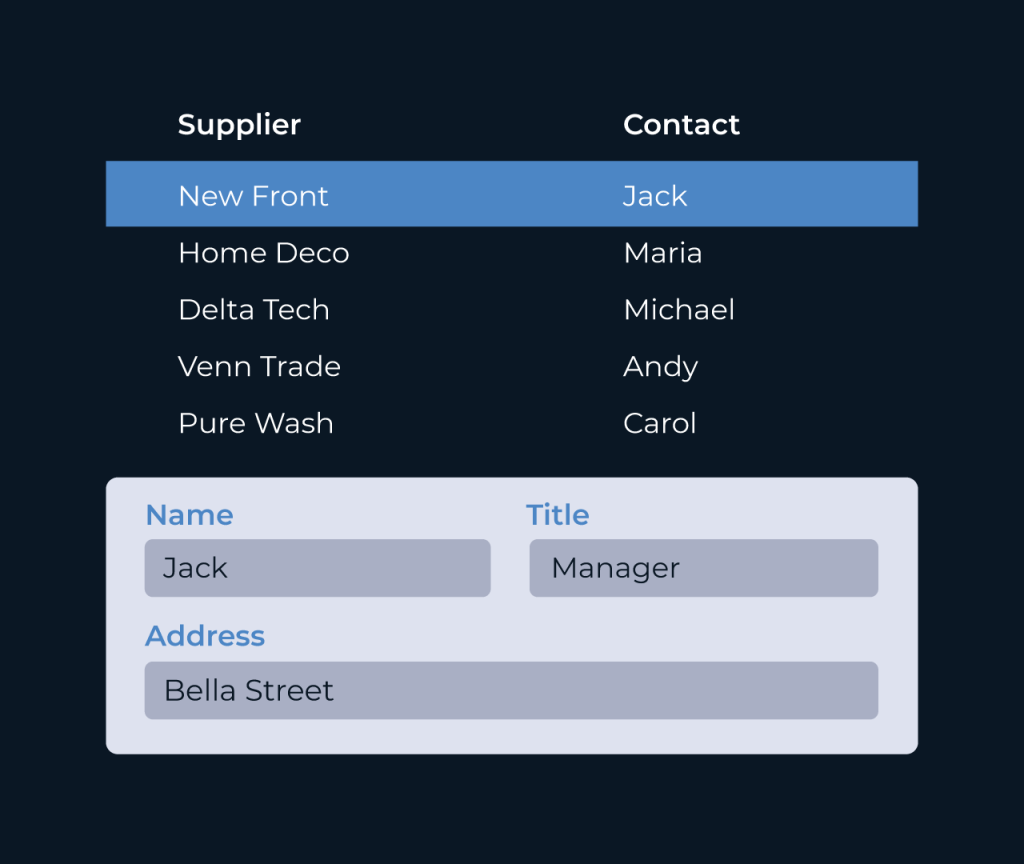
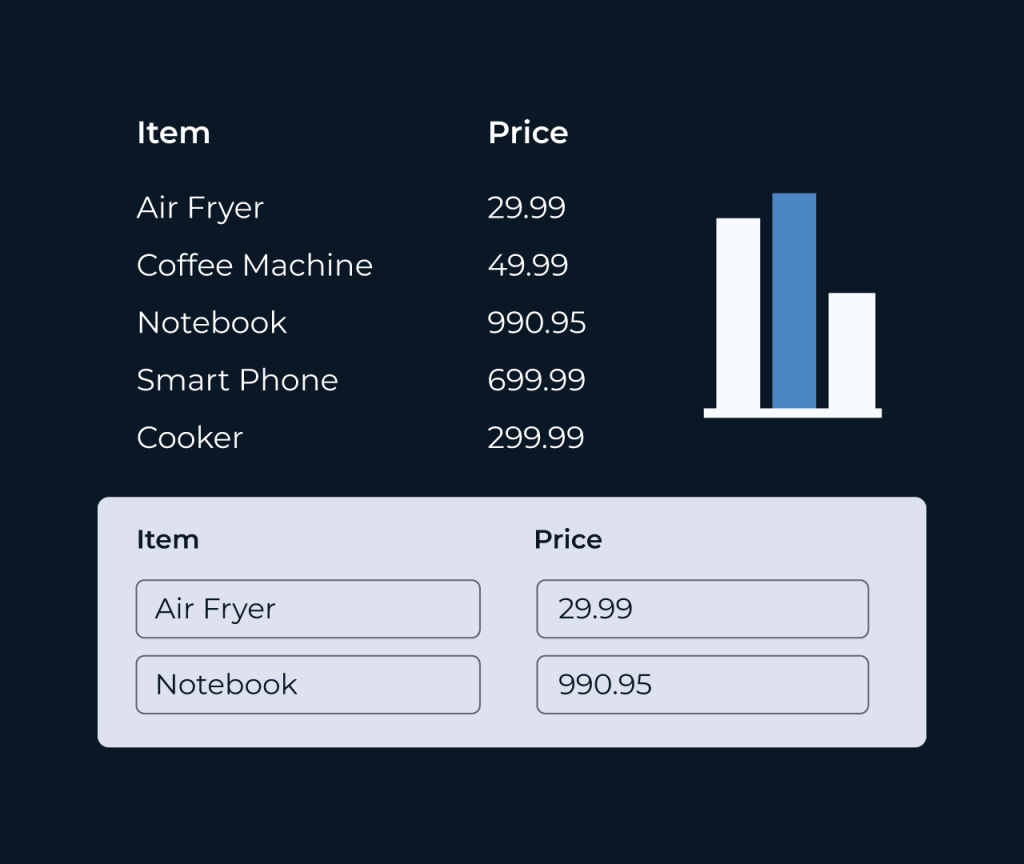
Create a Security Database
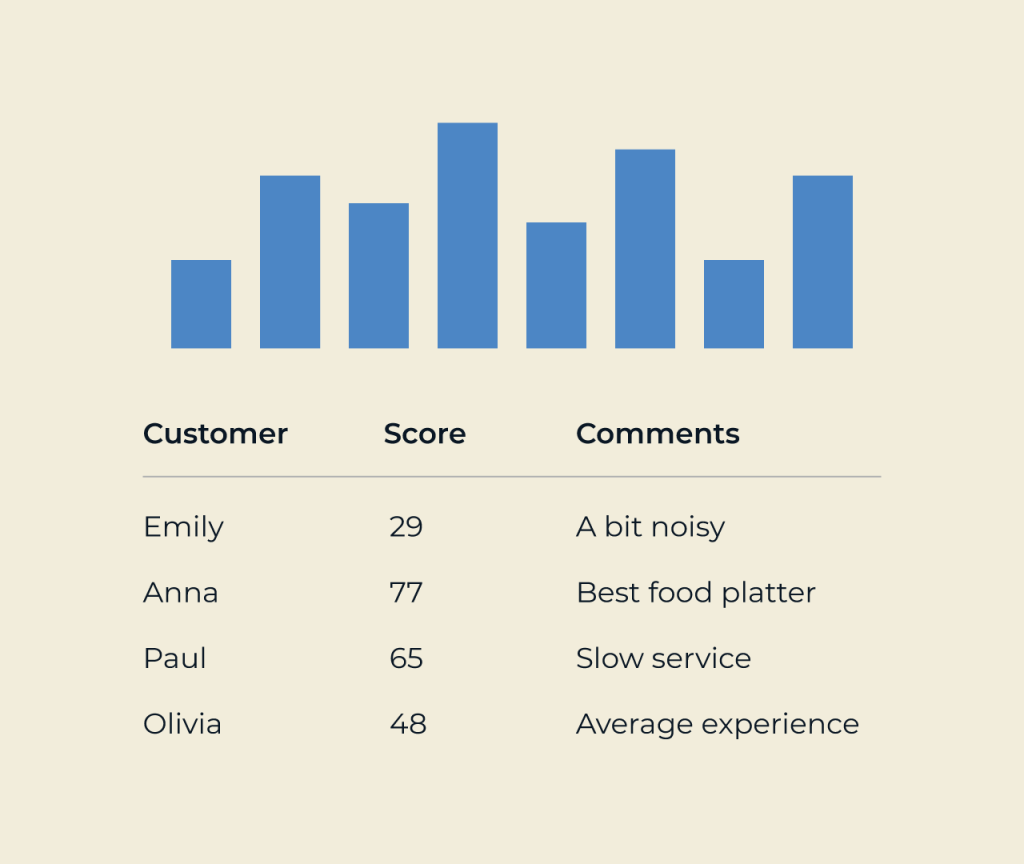
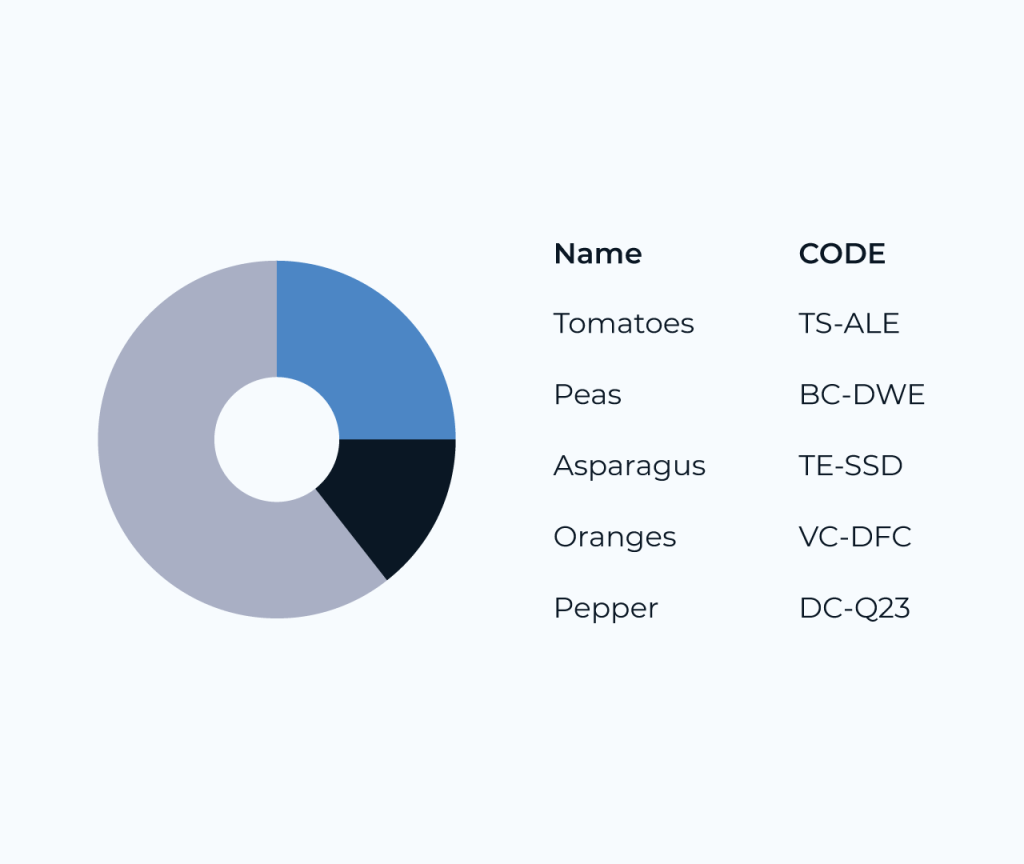
Creating a security database is essential for managing and safeguarding sensitive information. It serves as a centralized repository that helps organizations monitor access, track incidents, and ensure compliance with regulations. By utilizing a structured approach, businesses can enhance their security measures while providing clear visibility into potential vulnerabilities.
Five offers intuitive tools that enable seamless construction of security databases. With features like customizable fields, real-time analytics, and automated reporting, Five allows users to tailor their database to fit specific needs. This flexibility not only streamlines data management but also enhances decision-making processes, making security more proactive and efficient.