Create a Permission Database
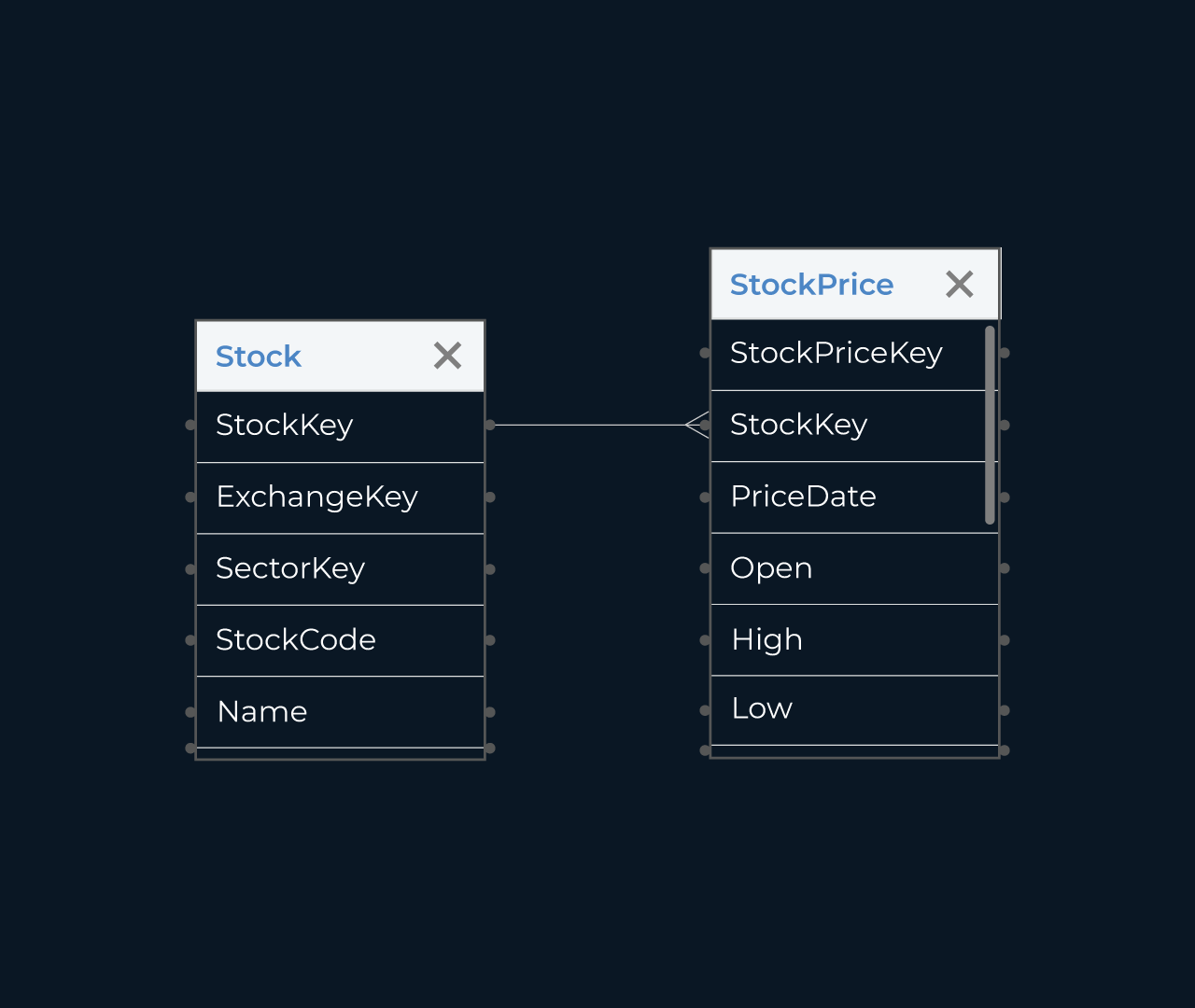
Creating a permission database is essential for managing user access and roles effectively. With Five, you can easily configure and customize permissions tailored to your organization’s specific needs. This robust framework allows administrators to define who can access what, ensuring both security and compliance.
Five’s intuitive interface enables users to build a detailed permission structure in just a few clicks. You can assign roles, set permissions for individual users or groups, and amend settings as required. This flexibility ensures that your organization maintains a streamlined workflow while safeguarding sensitive information.