Create a Security Portal
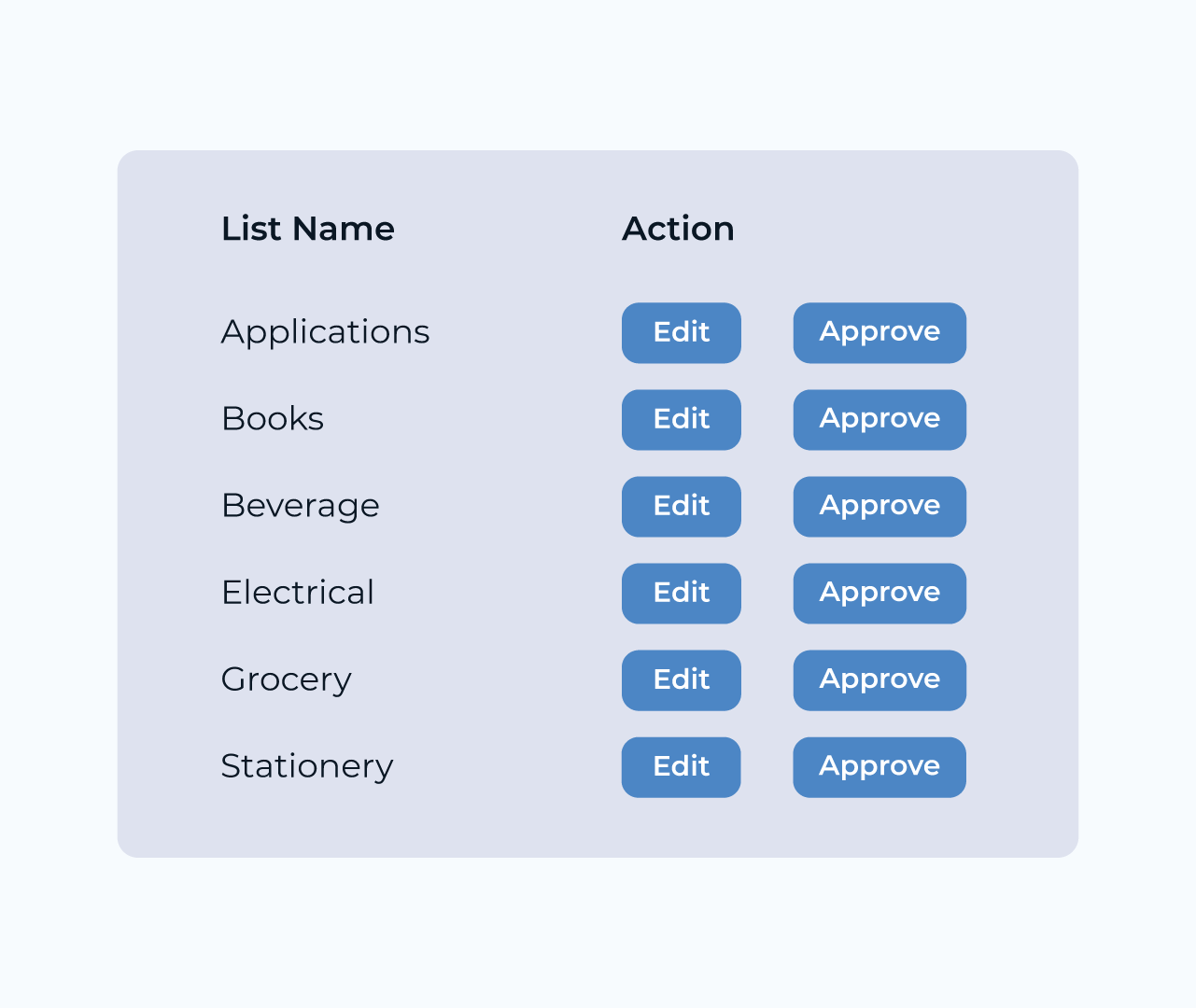
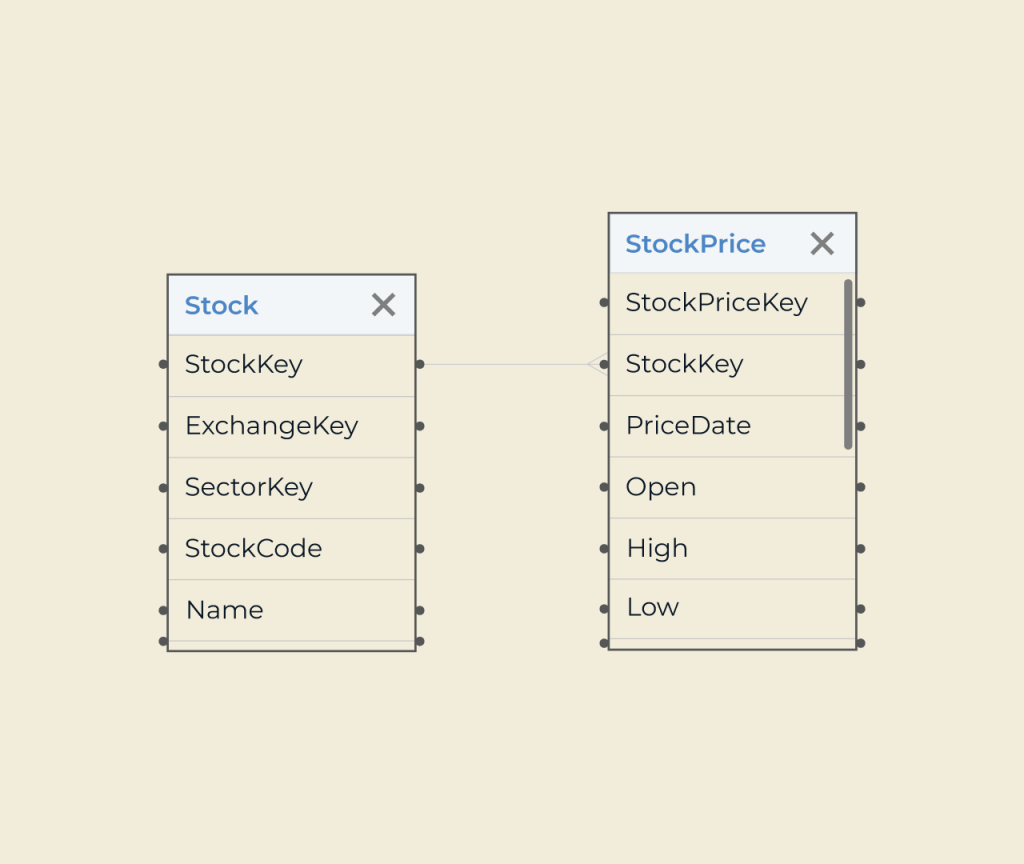
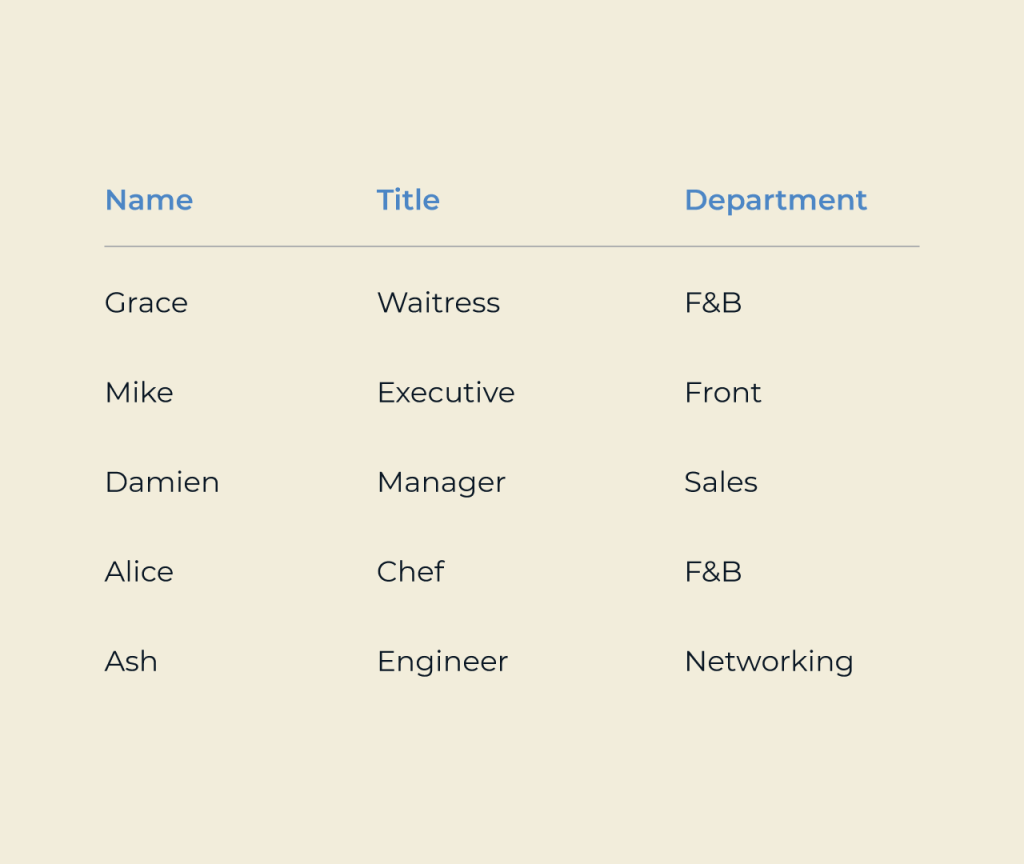
Creating a security portal is essential for safeguarding sensitive data and ensuring compliance with industry regulations. With Five’s intuitive platform, you can seamlessly develop a customized security portal tailored to your organization’s unique needs. Its user-friendly interface allows for straightforward integration of essential features like user authentication, access controls, and real-time monitoring.
Five empowers developers with robust tools and APIs, enabling the rapid deployment of security protocols without compromising on functionality. Whether you’re looking to enhance existing security measures or establish a new hub for user engagement, Five provides the flexibility and scalability necessary to create a comprehensive security portal that meets modern demands.